RapidFire Tools:
A Credential Nightmare.
Executive Summary
Critical security vulnerabilities identified in Kaseya's RapidFire Tools Network Detective, a widely-deployed MSP network assessment platform. Findings include cleartext credential storage and deterministic encryption allowing trivial password extraction from temporary files.
Cleartext Credential Storage
CVSS 8.2 (HIGH)
CVSS Vector: CVSS:3.1/AV:L/AC:L/PR:L/UI:R/S:C/C:H/I:H/A:H
Description
User-supplied credentials are stored in cleartext across multiple temporary files during scanning activities, including administrative account passwords without encryption or access controls.
Affected Files
- > collection.txt
- > ndfRun.log
- > run.ndp
- > ndscan-########.ndf (ZIP archive)
Default Storage Paths
%programfiles%\NetworkDetective\DataCollector\bin\tmp\ndc%AppData%\Local\Temp\
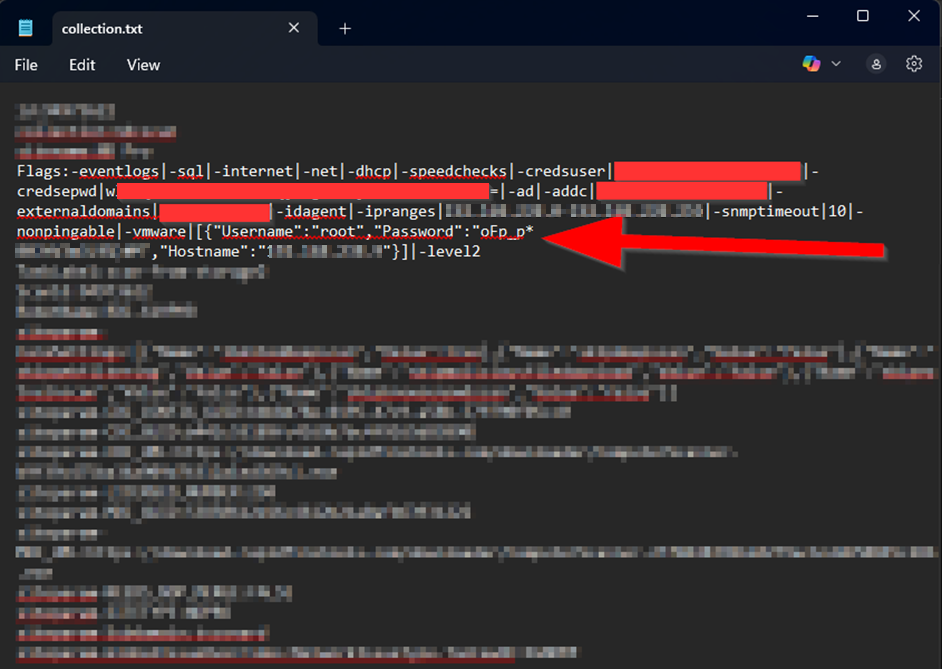
SCREENSHOT 1.1 // CLEARTEXT PASSWORD IN COLLECTION.TXT
SCREENSHOT 1.2 // KASEYA HELP ARTICLE REFERENCE
Predictable Encryption Weakness
CVSS 7.5 (HIGH)
CVSS Vector: CVSS:3.1/AV:L/AC:H/PR:L/UI:R/S:C/C:H/I:H/A:H
Description
Password encryption is performed using a deterministic, static approach with hardcoded values and static salts producing predictable and reversible ciphertext.
Affected Binary
RemoteDataCollectorSetup.exe
HARDCODED SALT VALUE: The salt value identified in the binary is the literal string "Ivan Medvedev"
The static nature of the encryption means that once the key derivation is understood, all encrypted credentials across all deployments can be decrypted with the same approach.
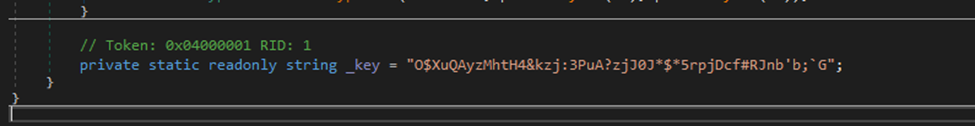
SCREENSHOT 2.1 // ENCRYPTION KEY WITHIN BINARY
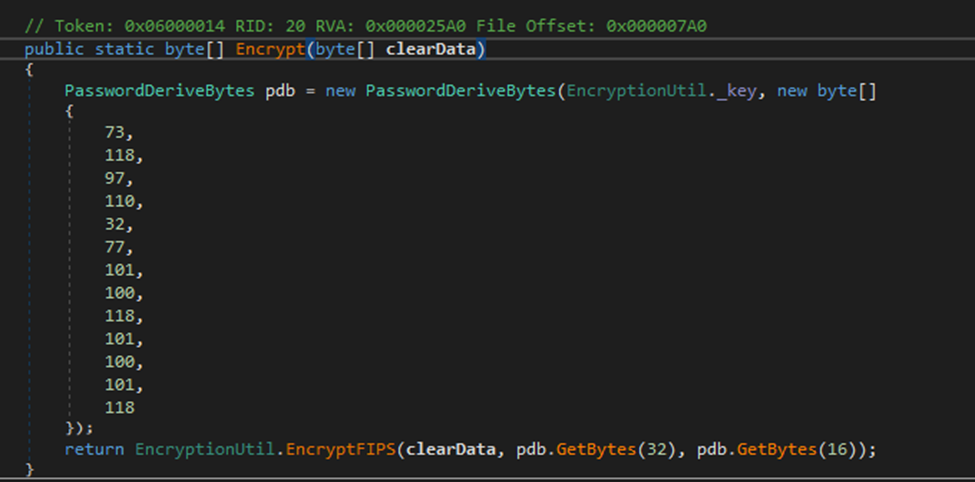
SCREENSHOT 2.2 // NON-FIPS ENCRYPT FUNCTION
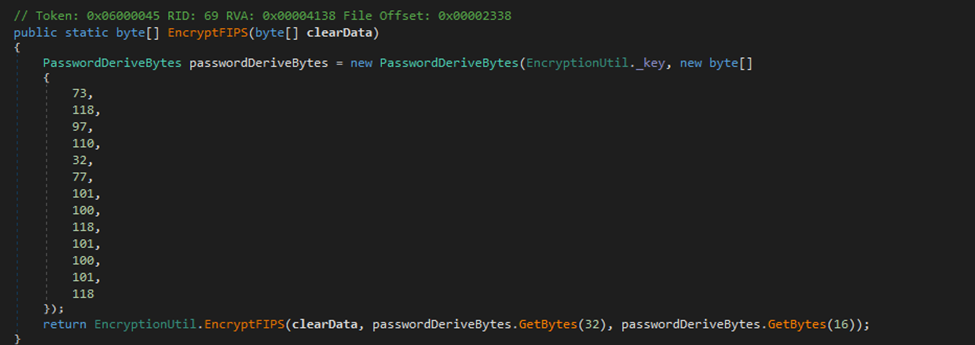
SCREENSHOT 2.3 // FIPS ENCRYPT FUNCTION
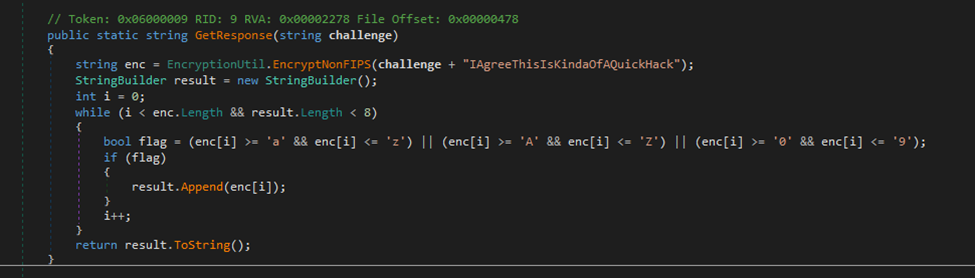
SCREENSHOT 2.4 // FIPS KEY STORAGE
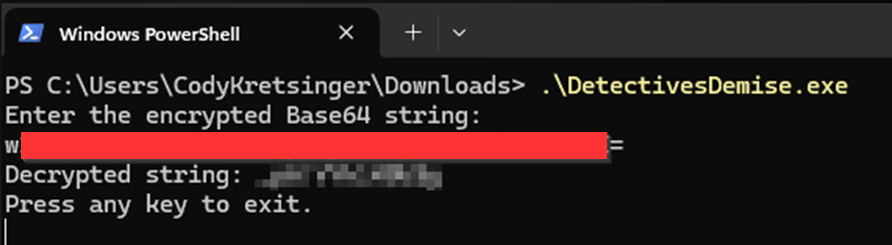
SCREENSHOT 2.5 // PASSWORD DECRYPTION DEMONSTRATION
Impact Assessment
Affects thousands of MSPs and MSSPs using Network Detective for customer assessments. Compromised workstations or persistent malware can harvest:
- > Domain administrator credentials
- > Service account passwords
- > Infrastructure access credentials
- > Customer network authentication tokens
Combined exploitation allows complete environment takeover across all customer networks scanned by affected tools.
Remediation
For Kaseya
- Eliminate plaintext password storage in all files
- Obscure or hash password data in logs/reports
- Prevent password artifacts from filesystem writes
- Replace deterministic key/IV derivation with secure random values
- Adopt authenticated encryption (AES-GCM)
- Eliminate static key material from binaries
- Ensure proper cryptographic role separation
// CUSTOMER ACTION ITEMS
- Update all on-premises RapidFire Tools instances immediately
- Verify directory absence:
%programfiles%\NetworkDetective\DataCollector\bin\tmp\ndc - Rotate all credentials previously used for network scans
- Audit scan workstations for signs of compromise
- Review access logs for unauthorized credential usage
Disclosure Timeline
2025-05-06 — Initial discovery
2025-05-19 — Vendor notification
2025-06-17 — CVE assignments received / vendor updated
2025-07-10 — Public disclosure