This Little Light of Mine,
I'm Going to Get it Pwned.

GRRCON 2022 // TALK ARTWORK
Joint research with Nick Schroeder examining critical security gaps in industrial lighting control systems deployed at high-profile landmarks, stadiums, and entertainment venues worldwide.
Video
Live demonstration of remotely controlling bridge lighting infrastructure. This demonstration was conducted legally with proper authorization.
DEMONSTRATION // AUTHORIZED BRIDGE LIGHTING CONTROL TEST
Affected Systems
ETC Mosaic Controllers
Architectural lighting control systems widely deployed in entertainment venues, museums, and architectural installations for DMX-based lighting automation.
Pharos LPC / TPC / MSC Controllers
Industrial controllers managing large-scale lighting installations on buildings, bridges, and public landmarks.
Vulnerability Details
Unauthenticated Information Disclosure
Mosaic and Pharos controllers display the controller type, software version, firmware version, and other identifying information without the requirement to login.
EXPOSED INFORMATION INCLUDES:
- > Log files
- > Controller configuration
- > Network information
- > Project details
- > Locale information
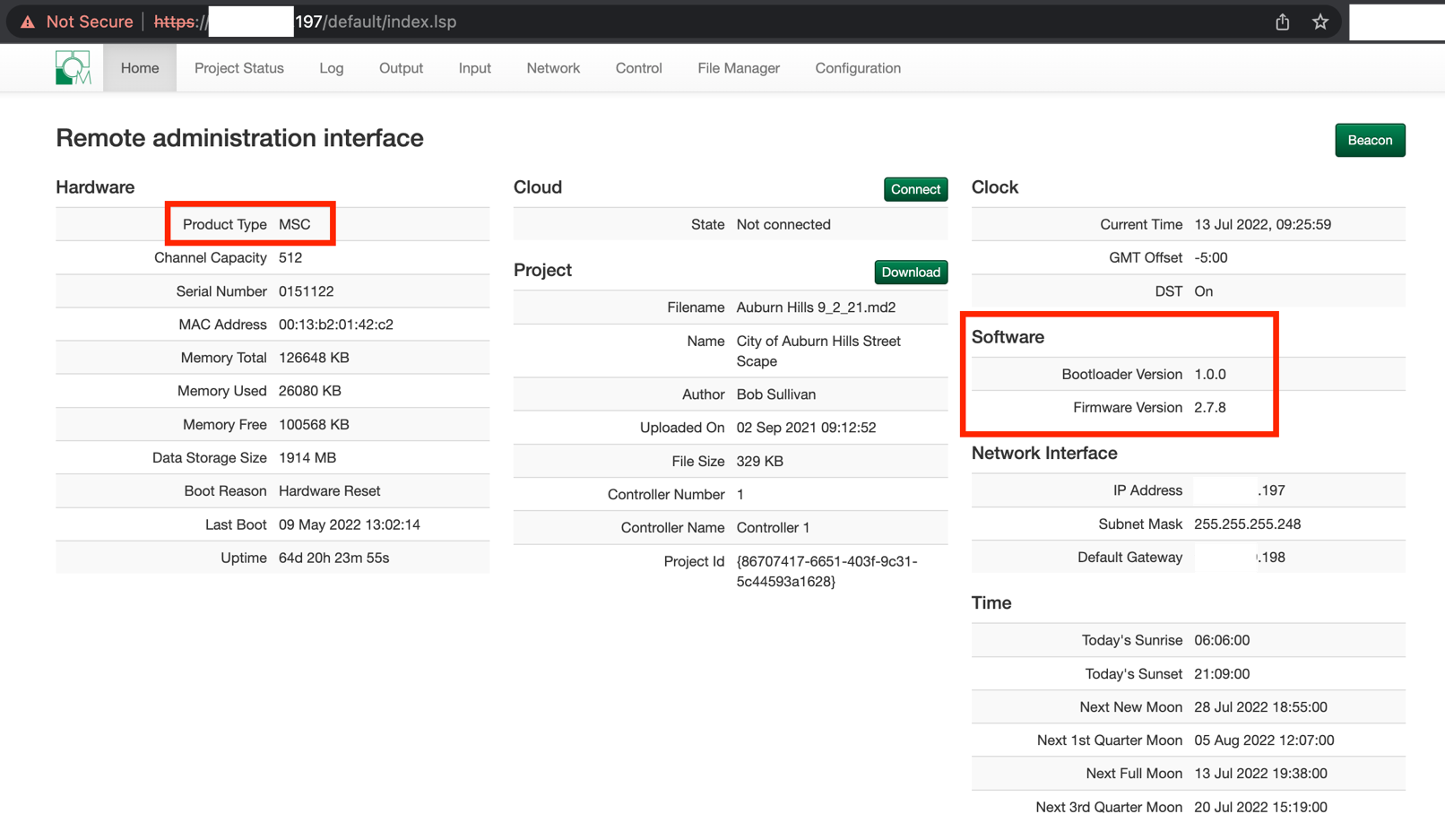
EVIDENCE // EXPOSED CONTROLLER INFO
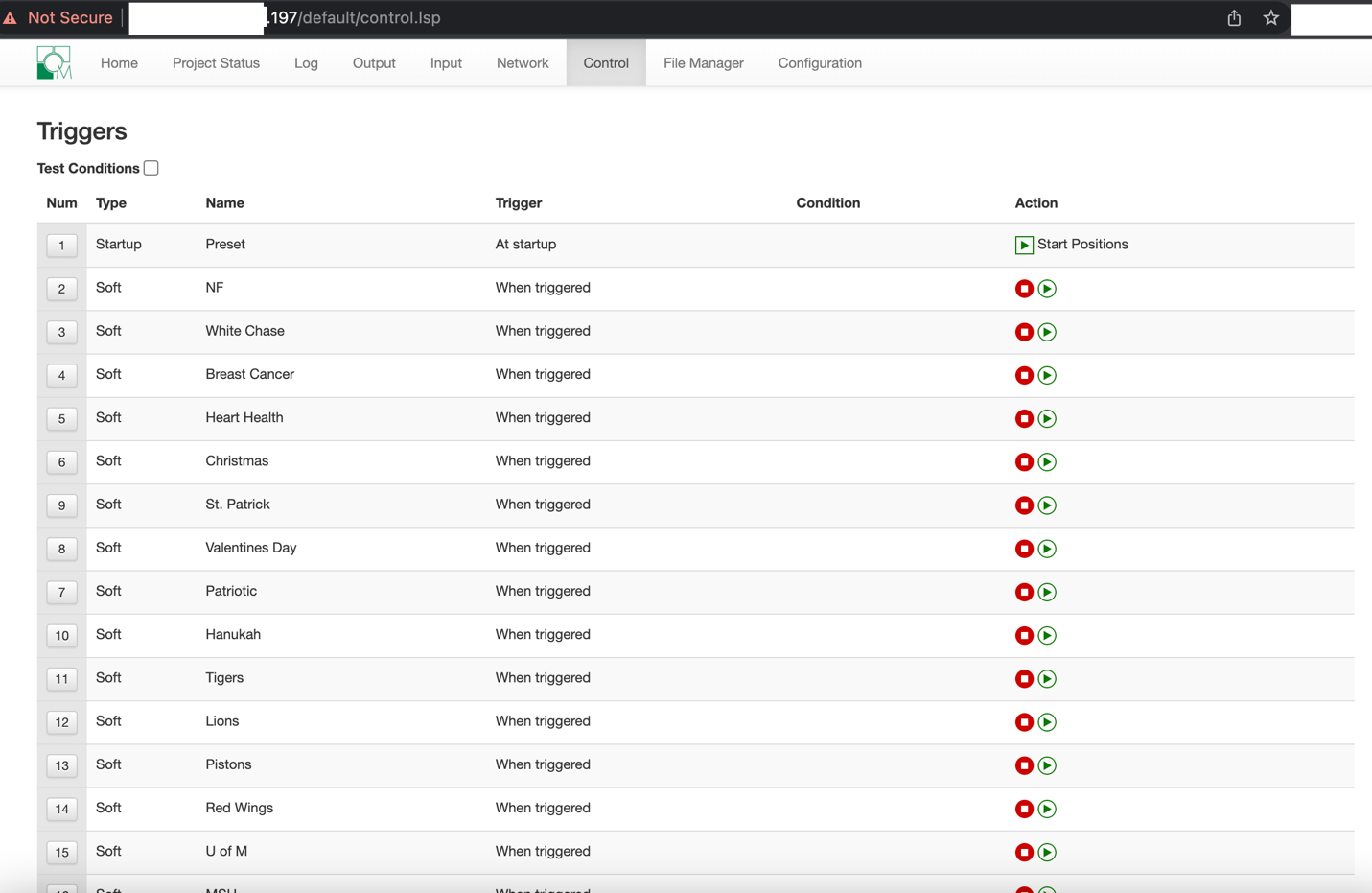
EVIDENCE // NETWORK CONFIGURATION
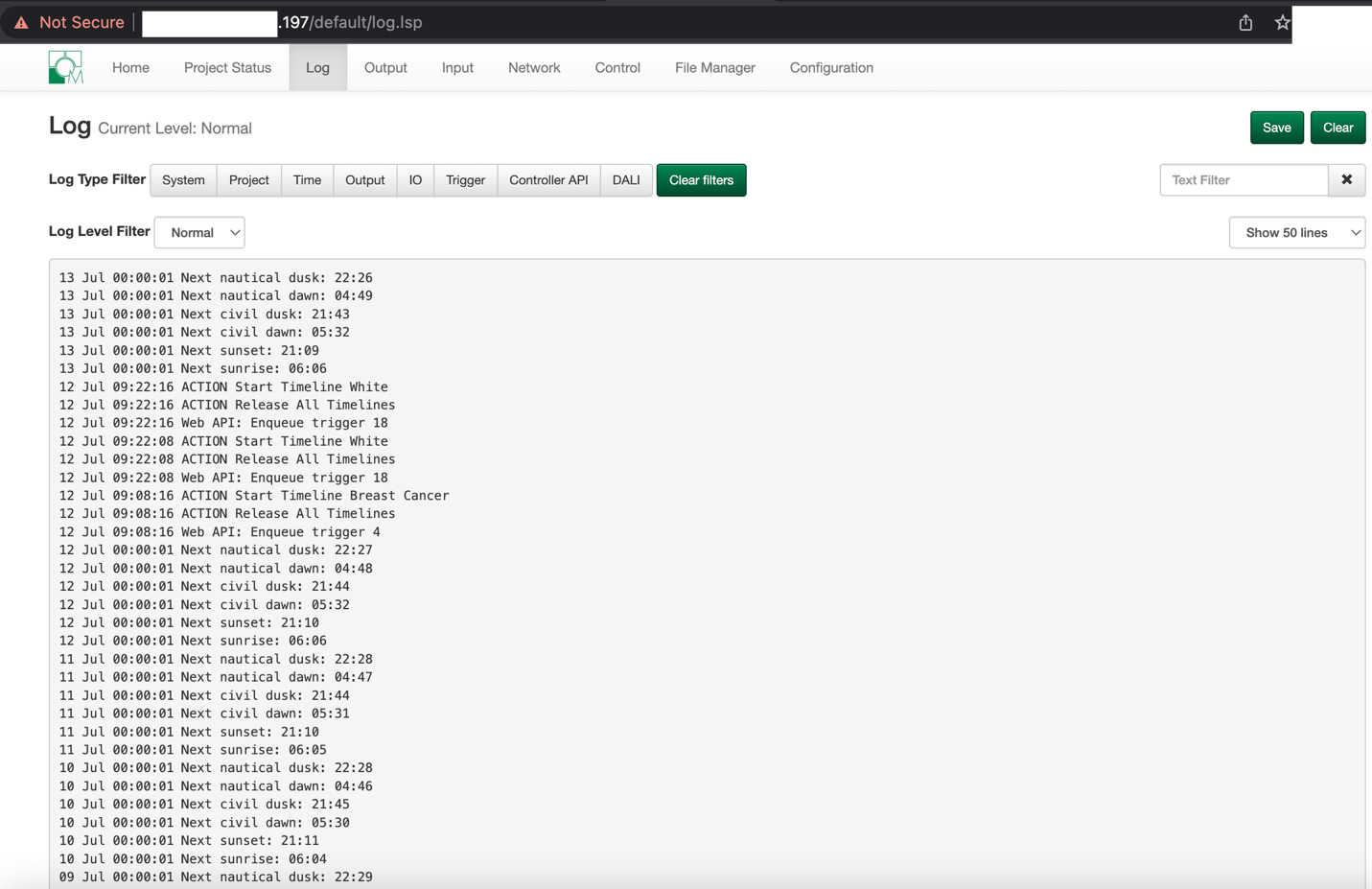
EVIDENCE // LOG FILE EXPOSURE
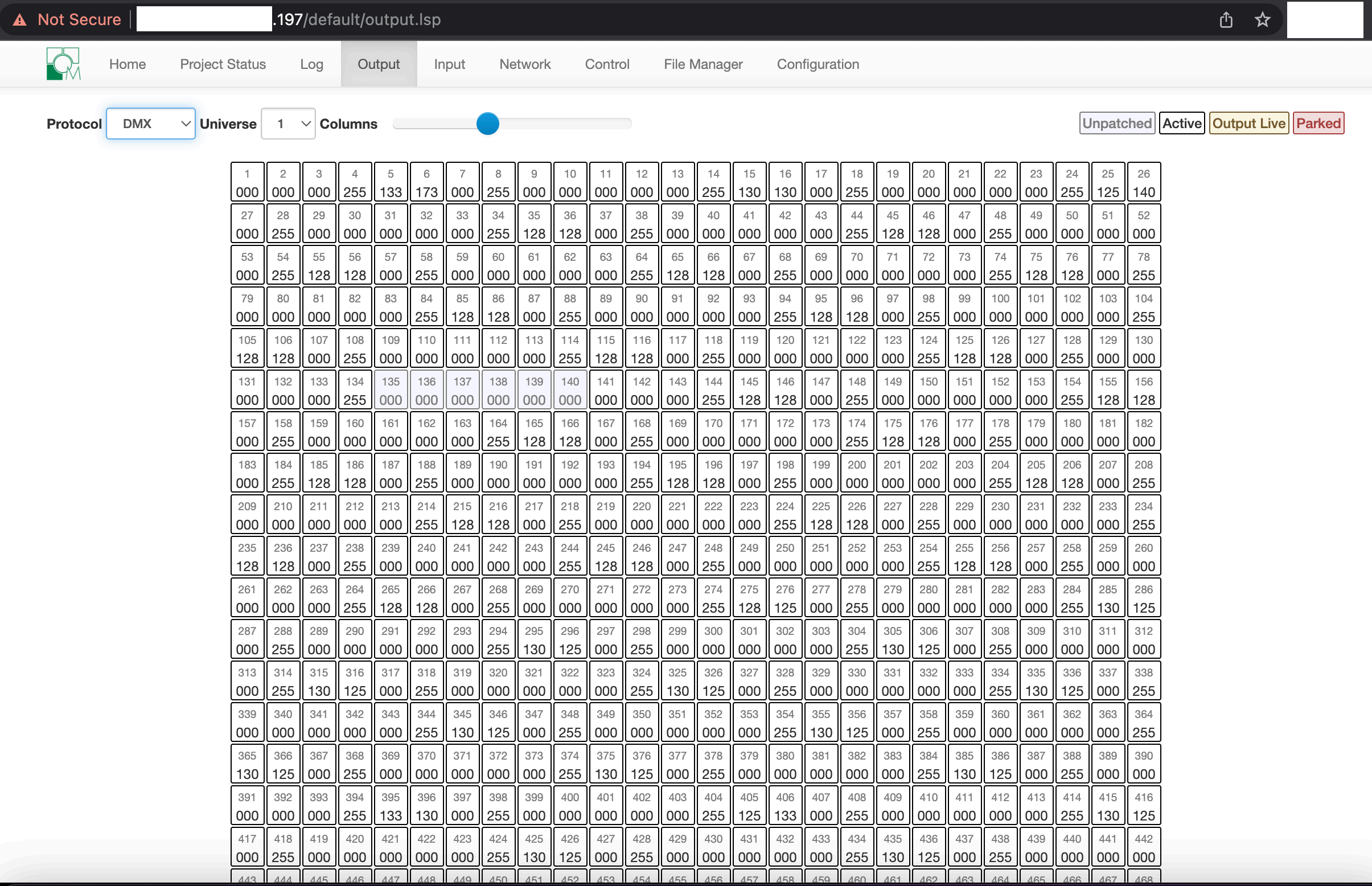
EVIDENCE // PROJECT DETAILS
Discovery Methods
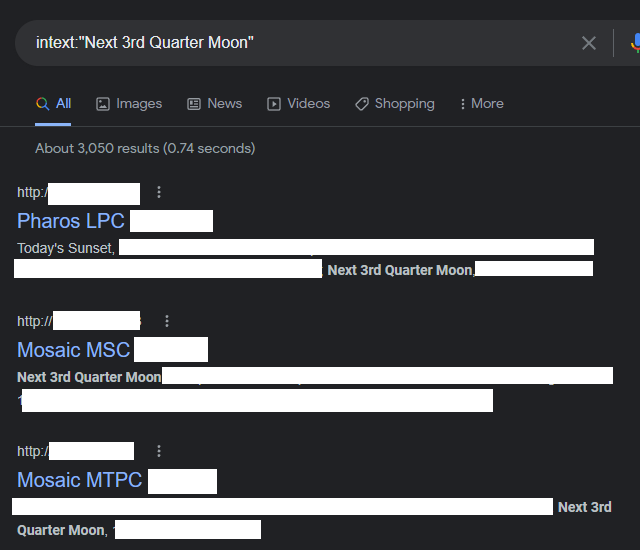
EVIDENCE // GOOGLE SEARCH RESULTS
Geographic Distribution
Approximately 50% of discovered devices were located in the United States. Belgium represented the second-highest concentration of exposed controllers.
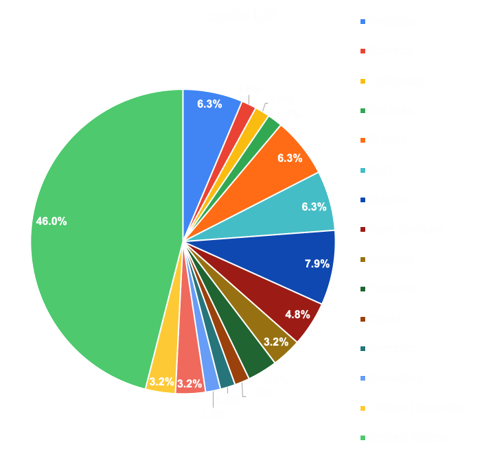
SHODAN // GEOGRAPHIC DISTRIBUTION
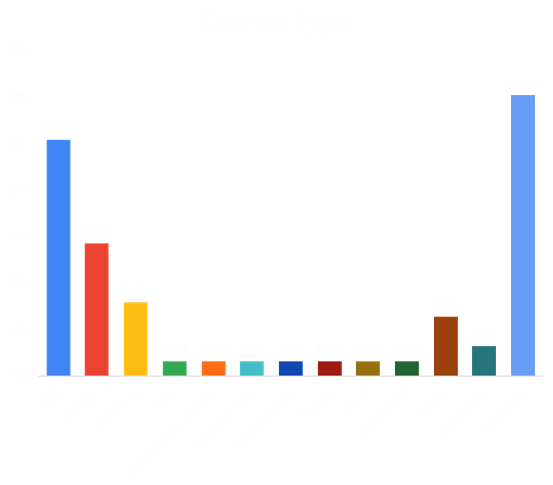
SHODAN // DEVICE STATISTICS
Additional Evidence
EVIDENCE // CONTROLLER INTERFACE
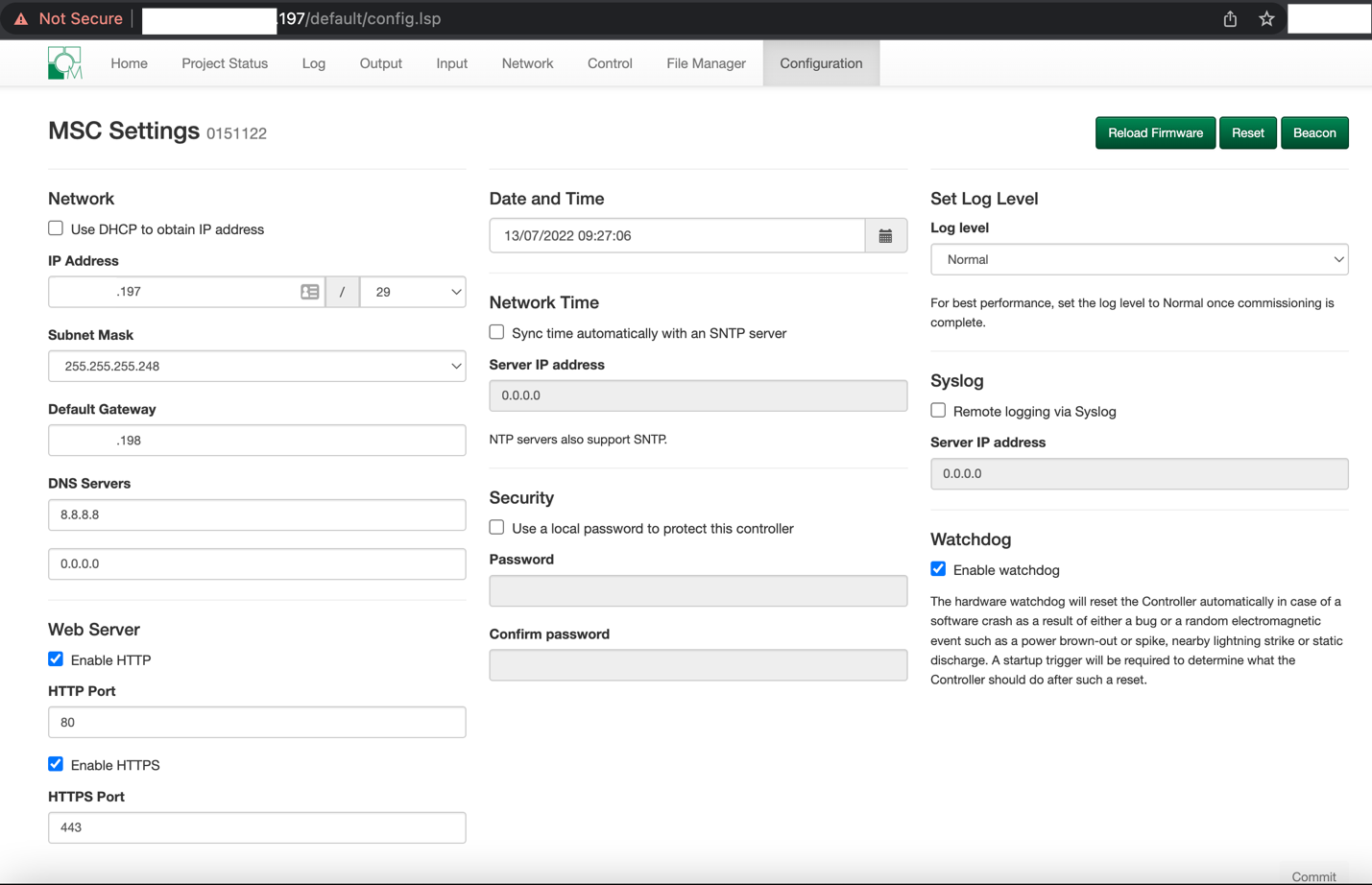
EVIDENCE // CONFIGURATION PANEL
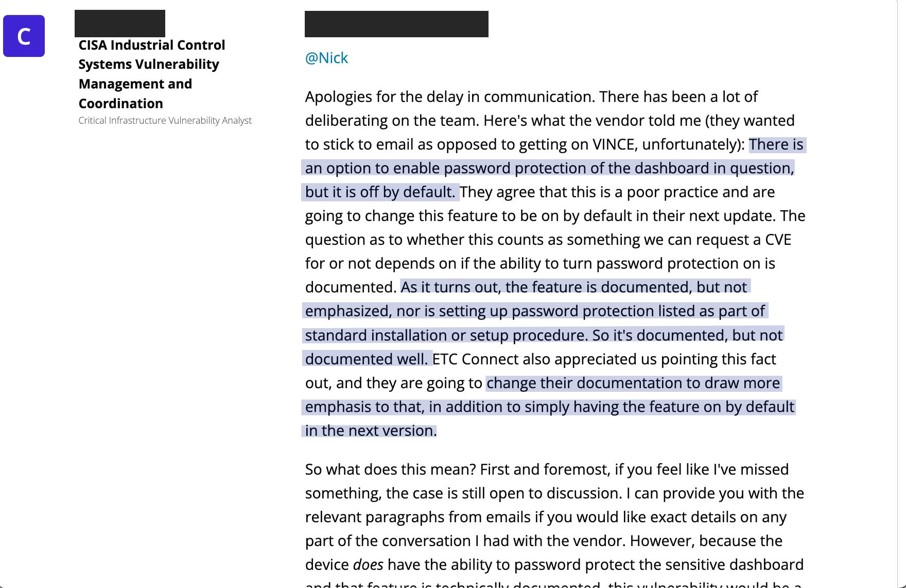
CONTEXT // REAL-WORLD INSTALLATION
Recommendations
- Stop deploying internet-connected hardware lacking authentication
- Implement vendor configuration best practices
- Place ICS/lighting controllers behind VPN or firewall
- Enable authentication on all web interfaces
- Conduct regular external exposure audits
- Monitor for unauthorized access attempts